2ez You Wished
2ez You Wished
In this walkthrough, we are going to solve a steganography challenge called
2ez_you_wished. As the name suggests, it is not your typical challenge and required keen observation.
Steganography is the practice of concealing a message within another message or object, making the hidden information undetectable without specific knowledge or tools.
Solving 2ez_you_wished
- We are first provided with a zip file named
2ez.zip. Download it and unzip it in your CTF/Steganography folder. its always nice to have clean working directories.
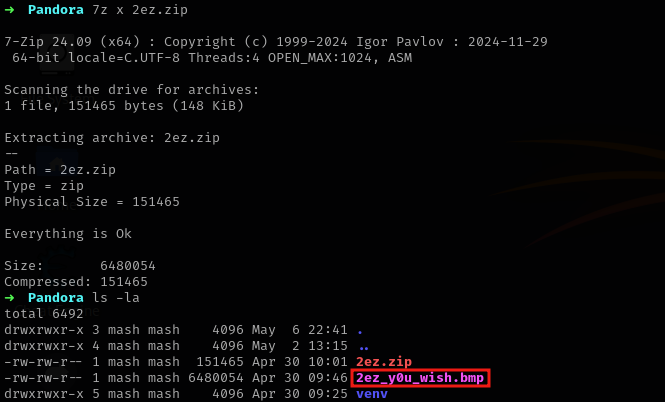
- We get an image
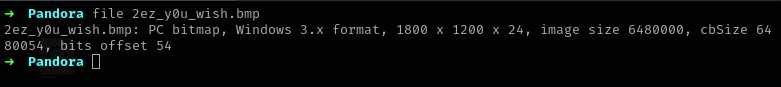
2ez_y0u_wish.bmp. - Running
file 2ez_y0u_wish.bmpreveals it is abitmapimage.
- We then proceed to run tools like
zstegto see whether we can find any hidden data.
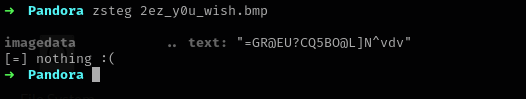
- Players were lost here, thinking the string was a hidden flag or hidden secret.
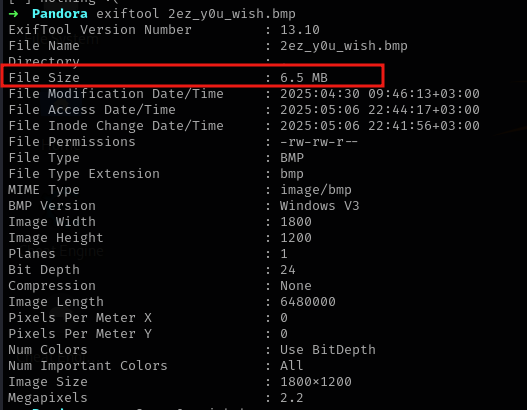
- One way of knowing that a file has been embedded in another is usually detected by checking the file size. First open the image as shown below.

- The image is very light from the looks of it, but running
exiftool 2ez_y0u_wish.bmpreveals that it’s file size is6.5 MB. Pretty sus, right?
- Now, let’s use stegseek to find hidden data within the image. Run
stegseek 2ez_y0u_wish.bmp.
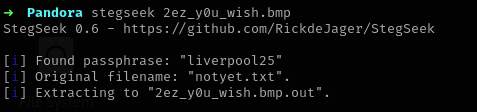
- Immedietely, we recover a passphrase
liverpool25which is then used to recover a filenotyet.txtthat is saved under2ez_y0u_wish.bmp.out. - Lets see the contents of the file by running
cat 2ez_y0u_wish.bmp.out.
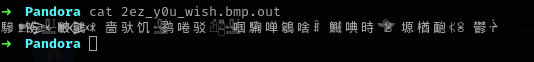
- Is that chinese, Korean or even Japanese?? Lets ask google translate.
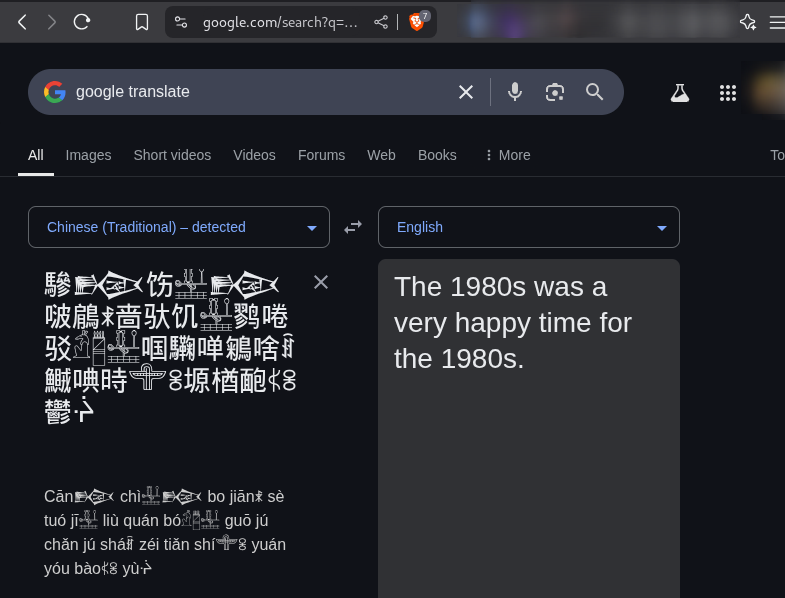
- What does
The 1980s was a very happy time for the 1980sthat even mean?? - That is where almost every player was lost. Is this an
OSINTchallenge or aSteganographychallenge. - Well, it was in the steganography challenge, and the author intended you to decode critical information from that text.
- Googling around you will find that there exists
base65536and using online decoders like Better Converter, you can decode the string.
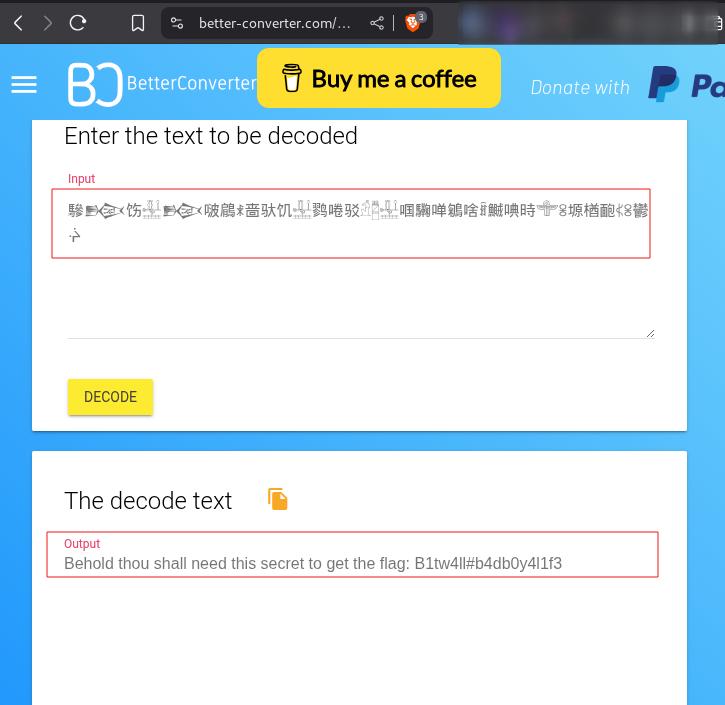
- And there we get a key
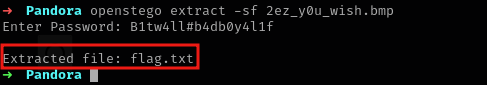
B1tw4ll#b4db0y4l1f3to the second part of the challenge…we are almost there. - After trying multiple tools, you should end up using
openstego. Either the GUI version or the CLI version should work just fine.
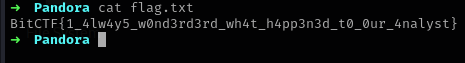
- Finally, we can read our flag!!.
Takeaways
This challenge demanded a great deal of critical thinking due to its numerous rabbit holes. All in all, steganography continues to play a crucial role in our everyday digital landscape.
This post is licensed under CC BY 4.0 by the author.